BabaYaga is the moniker of a new strain of WordPress malware that has been making a name for itself lately. It’s unusual because it is actually capable of removing other malware in order to easier infect your site. However, this doesn’t mean it’s friendly, or that it can’t do damage to your site.
In this article, we’re going to tell you everything you need to know about this new threat. We’ll be discussing how you can be affected by the BabaYaga malware, and provide you with recommendations to keep your site clean.
Let’s go!
Introducing the BabaYaga Malware
BabaYaga was recently introduced to the world thanks to a comprehensive report from Wordfence. According to the initial report, BabaYaga isn’t actually a new threat. However, it caught the attention of the team due to its unusually comprehensive methods for infecting sites:
None of these countermeasures are groundbreaking individually, but taken as a whole they comprise a suite of functionality unusually comprehensive and effective for spam droppers.
BabaYaga is also noteworthy in that it only targets WordPress sites. As such, it’s particularly resilient against many of the standard ways of detecting and removing malware. We’ve already discussed in previous articles about how WordPress malware is a serious problem, so you should always keep yourself up-to-date with the latest security threats. As such, let’s look a little closer at BabaYaga.
What BabaYaga Does to Your WordPress Site
The most prominent feature of the BabaYaga malware is its ability to get rid of its ‘competitors’. In short, BabaYaga eats other malware. While this may make it sound great, like having a friendly spider eating the flies in your house, it’s actually more insidious.
The reason BabaYaga gets rid of other malware is to keep itself hidden. As the white paper published by Wordfence says:
A good parasite wants to keep its host alive. If everything is up and working properly, the owner of an affected site can go without knowing anything is wrong indefinitely.
Essentially, if malware makes its own existence obvious, the owner of the site is likely to scrub their site of all malicious programs. BabaYaga therefore silently removes these other threats so you won’t notice it’s there.
However, what does it actually do? Once BabaYaga has infected your site, it will begin to generate spam content. The generated pages will be full of keyword stuffing, which will obviously show up in search engines. If someone were to click a link, they’d be taken to an external affiliate site. Essentially, it’s a way to use your site to drive dishonest traffic towards their affiliate links in an attempt to fool careless users.
Naturally, this can severely hurt your site’s Search Engine Optimization (SEO). It could also negatively affect your bandwidth and storage, while making your site vulnerable to other security threats.
How to Spot If BabaYaga Has Infected Your Site
The BabaYaga white paper outlines a number of indicators of a compromised site. First of all, if your server is contacting the following host or IP, your site is most likely infected:
- 7od.info (178.132.0.105)
- my.wpssi.com (89.38.98.31)
You should also perform a Google search to see if your site is producing spam content. You can do this by going to Google and searching for site:https://yoursiteurlhere.com (obviously replacing the placeholder with your own site). If you find several pages you do not recognize that are clearly spam, you can be sure BabaYaga has affected your site:
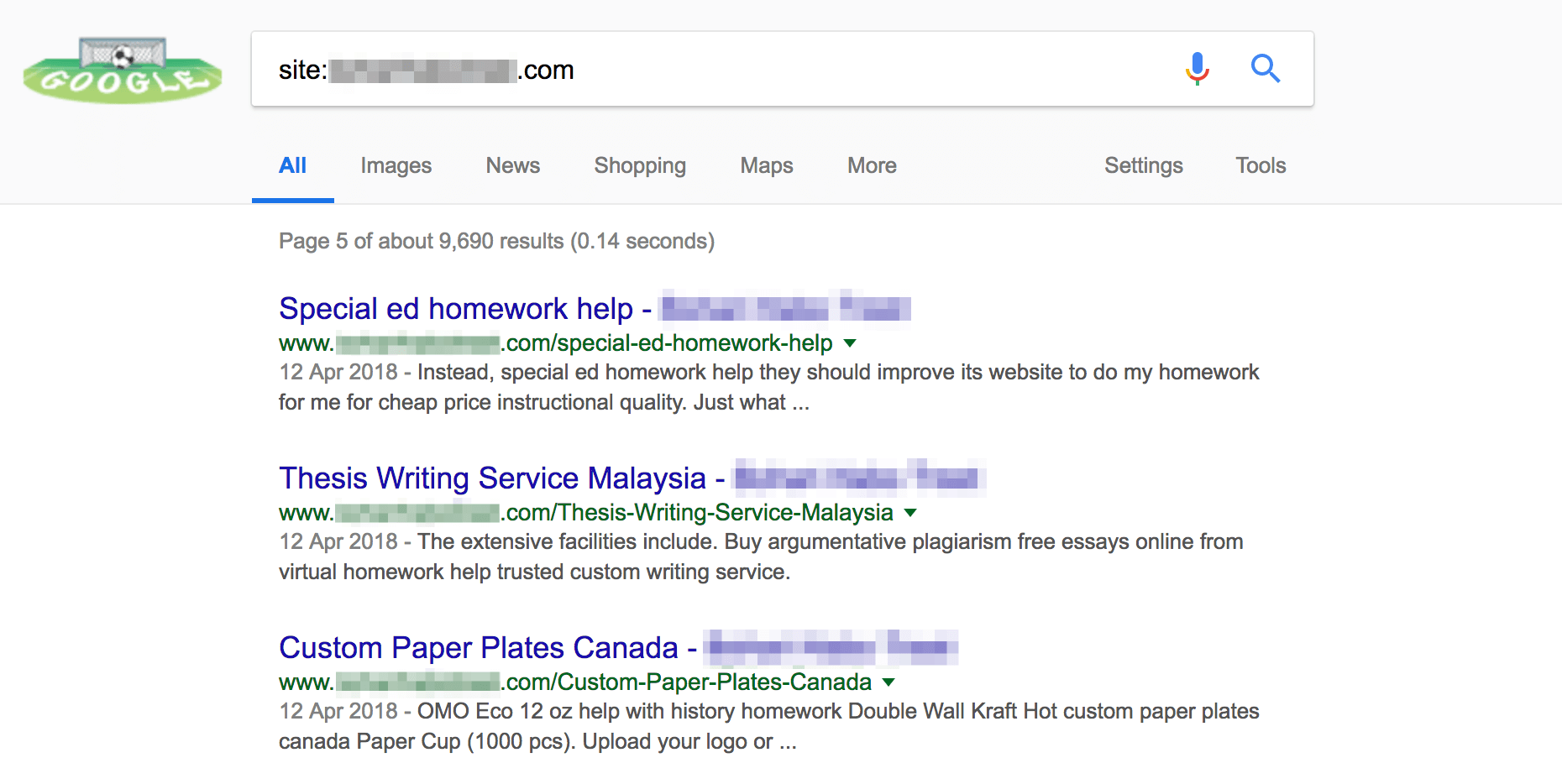
If you find that BabaYaga has got the worst of you, it’s time to clean up your site. You should start by running an anti-virus scan on your local machine, followed by changing all of your relevant passwords. This includes for your site, your File Transfer Protocol (FTP) credentials, and your server. You may also want to revert your site to a previous backup.
Because BabaYaga is unusually resilient, you may need to spend some time on scrubbing your site clean. You might even want to consider reaching out to Wordfence to help you clean your site if your efforts aren’t enough. We’ve recommended them before, and we don’t mind doing so again!
How to Protect Your Site From BabaYaga (And Other Malware)
If you’re fortunate in that your site hasn’t been infected by BabaYaga, this doesn’t mean you can relax just yet. In fact, your next step should be to ensure your site is protected. However, this doesn’t have to be a difficult process.
While BabaYaga is a particularly sly and difficult to detect malware, it’s still just malware. As such, you can deal with and stop it similarly to others. To prevent your site from being infected, you should make sure your site is secure in general.
We’ve discussed keeping your site secure before, so let us quickly recap some main points:
- Install a firewall and other security measures.
- Always use strong passwords and usernames for your WordPress site.
- Make sure your login screen is secure and stands up to brute force attacks.
- Scan your site for malware regularly.
- Keep WordPress, including your theme and plugins, updated at all times.
It’s also worth remembering that no security is perfect or everlasting. You need to keep up with new threats constantly, as attackers are always evolving their strategies. Even if you manage to stop BabaYaga at the door, there will always be new malware to follow tand be equally vigilant towards.
Conclusion
While WordPress is a secure platform at its core, there’s no shortage of malicious software trying to exploit it. The latest in line is BabaYaga, a type of malware that deletes other malware before infecting your site.
In this article, we’ve discussed the BabaYaga malware and how it can affect your WordPress site. We’ve also taken you through how to spot if this particularly elusive attacker has infected your site, and how you can get rid of it. Stay safe!
Do you have any questions about the BabaYaga malware and how to protect your site against it? Let us know in the comments section below!
Article thumbnail image by GoodStudio / shutterstock.com





Hello can I use your article on my site to educate my readers about this virus? I will give you full credit as the source. Kindly email me.
I searched site:https://bugouttips.com and google just scratched their head and said no results
Alan, I’ve just took a look and have received a page of results. Have another go, but it looks as though you’re safe. 🙂
Babayaga is the latest WordPress malware which generates spam contents once it gets to your website. It will just do keyword stuffing resulting in ranking your website. To keep your site from infected with malware you should install a firewall in your site.
Great article John,
I had an end user that insisted on maintaining his site and he got hit. He only used a simple password and out of date plugins. His reply was he is too busy to maintain it. Well Duh? Lesson learned.
Keep the good articles coming. I’m sharing this one.
All the best!
Rick
Thank you very much, Rick. I’m glad you liked the article. 🙂
This is scary stuff to hear what this malware does, one question do they ever catch the culprits who are developing this malware.
It sure is. Some malware creators do eventually get caught, such as the person behind “Fruitfly”: https://www.engadget.com/2018/01/10/doj-charges-creator-of-fruitfly-malware/
However, even if they are, the damage is usually already done unfortunately.
scary stuff… keep clean backups and keep a close eye on your site! considering the number of people in the various FB groups im in its still quite rare to see a “ive been hacked” post which is good.
Good article, I read the original over at Wordfence.
I have one site that was infected with the BabaYaga malware. It was a pain in the butt.
We ended up restoring a 6 month old backup of the site and installed Wordfence.
All is good so far, but those dodgy SEO links took a few weeks to start disappearing from Google search results.
Thank you, Shane. I’m sorry to hear you had to struggle with BabaYaga, but I’m also glad you managed to get it working in the end. 🙂
Clear! Thank you, for the post and the link.
I will tell my friends and associates. I was wondering, if this also acts like a worm traveling to one wp site to another when a link is established? I’m guessing “Yes, it will” and making sure the backlinks or posts watch. I will reread about posts and how to refine it to make sure that posters’ posts are authorized after review.
You’re welcome, Everett. Glad you found it useful. 🙂
As for your question, I’ll just quote WordFence’s white paper directly:
“The malware is able to search for other sites and run its infection routine on them as well. It traverses up as many levels as the attacker has specified, and looks for common names of website root directories like public_html, httpdocs, and so on. It also searches for directories that are named for domains. This allows the malware to spread to other websites on the same server.”
Thanks for this article. It’s very important to keep plugins updated, but sometimes site owners are fooled when there is no update available for a plugin, when the truth is that the plugin has been abandoned by the developers… thus, there may be security issues with it, but no update will ever be generated. Some plugins in the WordPress repository have not had any updates in over 7 years. Any plugin that is being actively supported and developed will have updates every few months, or at least once a year. There is a free plugin called “Vendi Abandoned Plugin Check” that I install on every client WP install. It’s a lightweight plugin that will check for the last time every plugin was updated, and display a red warning if any plugin has not been updated in over a year (and will display the number of days since the last update). Another advantage to knowing this information is compatibility with WP and your Themes. If a plugin hasn’t been updated in years, it is likely going to give you issues. I hope this helps! Disclosure: I have no interest in the plugin mentioned, just a happy user. The plugin is free and has no paid option.
You’re very welcome, Scott. You raise a good point there, and it’s important to regularly check your installed plugins and themes to ensure they’re still secure. Thank you for your recommendation. 🙂
Good points Scott. I typically won’t consider any plugins that haven’t been updated in a year. WordPress should really remove any outdated plugins which have not been tested with the current version of WP.
Kudos John for the write-up, same for the Wordfence team keeping the WordPress ecosystem safe. Here is my take, the end-clients of the creators of this malwares are as guilty and share a large part of the blame. If you ever need to drive traffic to your site, please make use of a reputable agency known for employing ethical means.
You’re welcome, Zion, and thank you for your comment! 🙂
So true, I have seen keyword infections for big hotel chains, name brand products and theme parks. I always wondered how in the world are these companies selecting their “SEO” services.
Any recommended solutions for protection would be helpful.
Recommended plugins to protect and firewall or sites.
Thanks for the heads-up on the latest Malware.
Hi Dean,
We’ve covered a few good options on the blog over the years. For example, WordFence remains a firm favorite. If you want more information on dealing with malware, perhaps these articles can be helpful:
https://www.elegantthemes.com/blog/tips-tricks/the-5-essential-wordpress-security-measures-you-must-take-and-how-to-implement-them
https://www.elegantthemes.com/blog/resources/a-collection-of-the-best-wordpress-security-plugins
Hey Dean. Ive been using iThemes Security for a while but I recently moved to using Malcare and BlogVault. Great service and great value. Highly recommended this combo. They also support easy staging sites for upgrading plugins etc and have a plugin called migrate guru that is fantastic. Hope this helps.
Wordfence has a WordPress security plugin that includes brute-force protection, a firewall, malware scans, IP blocking etc.
They are the best I have come across by far.
Hey Dean,
There are lots of security plugins out there, and they do a lot, but honestly they are not a full security solution, you need more than that, a decent server architecture or hosting company is the most important I thing to invest in, things outside of WordPress plugins, as they can only do so much.
We use CuroHosting who give a 100% guarantee so they deal with the problems which saves us a lot of headache.
I hope that helps. If not that company I would recommend looking at Managed WordPress Hosting in general, see what people are offering in terms of security, I think it’s much more than you would think these days.
Thanks
David